6.8 KiB
EasyTier
EasyTier is a simple, safe and decentralized VPN networking solution implemented with the Rust language and Tokio framework.
Features
- Decentralized: No need to rely on centralized services, nodes are equal and independent.
- Safe: Use WireGuard protocol to encrypt data.
- Cross-platform: Supports MacOS/Linux/Windows, will support IOS and Android in the future. The executable file is statically linked, making deployment simple.
- Networking without public IP: Supports networking using shared public nodes, refer to Configuration Guide
- NAT traversal: Supports UDP-based NAT traversal, able to establish stable connections even in complex network environments.
- Subnet Proxy (Point-to-Network): Nodes can expose accessible network segments as proxies to the VPN subnet, allowing other nodes to access these subnets through the node.
- Smart Routing: Selects links based on traffic to reduce latency and increase throughput.
- TCP Support: Provides reliable data transmission through concurrent TCP links when UDP is limited, optimizing performance.
- High Availability: Supports multi-path and switches to healthy paths when high packet loss or network errors are detected.
Installation
-
Download the precompiled binary file
Visit the GitHub Release page to download the binary file suitable for your operating system.
-
Install via crates.io
cargo install easytier -
Install from source code
cargo install --git https://github.com/KKRainbow/EasyTier.git
Quick Start
Make sure EasyTier is installed according to the Installation Guide, and both easytier-core and easytier-cli commands are available.
Two-node Networking
Assuming the network topology of the two nodes is as follows
flowchart LR
subgraph Node A IP 22.1.1.1
nodea[EasyTier\n10.144.144.1]
end
subgraph Node B
nodeb[EasyTier\n10.144.144.2]
end
nodea <-----> nodeb
-
Execute on Node A:
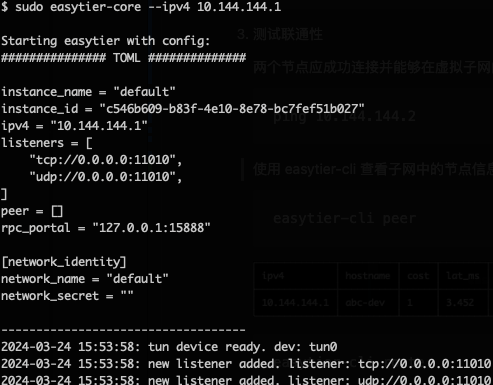
sudo easytier-core --ipv4 10.144.144.1Successful execution of the command will print the following.
-
Execute on Node B
sudo easytier-core --ipv4 10.144.144.2 --peers udp://22.1.1.1:11010 -
Test Connectivity
The two nodes should connect successfully and be able to communicate within the virtual subnet
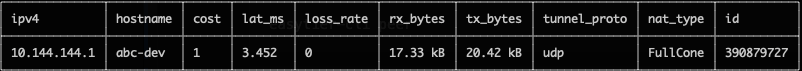
ping 10.144.144.2Use easytier-cli to view node information in the subnet
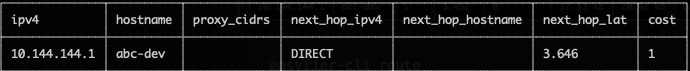
easytier-cli peereasytier-cli route
Multi-node Networking
Based on the two-node networking example just now, if more nodes need to join the virtual network, you can use the following command.
sudo easytier-core --ipv4 10.144.144.2 --peers udp://22.1.1.1:11010
The --peers parameter can fill in the listening address of any node already in the virtual network.
Subnet Proxy (Point-to-Network) Configuration
Assuming the network topology is as follows, Node B wants to share its accessible subnet 10.1.1.0/24 with other nodes.
flowchart LR
subgraph Node A IP 22.1.1.1
nodea[EasyTier\n10.144.144.1]
end
subgraph Node B
nodeb[EasyTier\n10.144.144.2]
end
id1[[10.1.1.0/24]]
nodea <--> nodeb <-.-> id1
Then the startup parameters for Node B's easytier are (new -n parameter)
sudo easytier-core --ipv4 10.144.144.2 -n 10.1.1.0/24
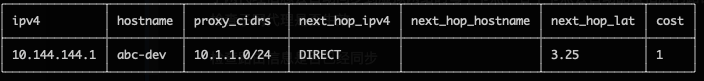
Subnet proxy information will automatically sync to each node in the virtual network, and each node will automatically configure the corresponding route. Node A can check whether the subnet proxy is effective through the following command.
-
Check whether the routing information has been synchronized, the proxy_cidrs column shows the proxied subnets.
easytier-cli route -
Test whether Node A can access nodes under the proxied subnet
ping 10.1.1.2
Networking without Public IP
EasyTier supports networking using shared public nodes. The currently deployed shared public node is tcp://easytier.public.kkrainbow.top:11010.
When using shared nodes, each node entering the network needs to provide the same --network-name and --network-secret parameters as the unique identifier of the network.
Taking two nodes as an example, Node A executes:
sudo easytier-core -i 10.144.144.1 --network-name abc --network-secret abc -e 'tcp://easytier.public.kkrainbow.top:11010'
Node B executes
sudo easytier-core --ipv4 10.144.144.2 --network-name abc --network-secret abc -e 'tcp://easytier.public.kkrainbow.top:11010'
After the command is successfully executed, Node A can access Node B through the virtual IP 10.144.144.2.
Configurations
You can use easytier-core --help to view all configuration items
Roadmap
- Improve documentation and user guides.
- Support features such as encryption, TCP hole punching, etc.
- Support Android, IOS and other mobile platforms.
- Support Web configuration management.
Community and Contribution
We welcome and encourage community contributions! If you want to get involved, please submit a GitHub PR. Detailed contribution guidelines can be found in CONTRIBUTING.md.
Related Projects and Resources
- ZeroTier: A global virtual network for connecting devices.
- TailScale: A VPN solution aimed at simplifying network configuration.
- vpncloud: A P2P Mesh VPN
License
EasyTier is released under the Apache License 2.0.
Contact
- Ask questions or report problems: GitHub Issues
- Discussion and exchange: GitHub Discussions
- QQ Group: 949700262